CI/CD – What You Need to Know
Continuous integration (CI) and continuous delivery or deployment (CD) cover the process of automatically merging, building, and testing code changes ready for release, and – in…
Whether you are just starting your observability journey or already are an expert, our courses will help advance your knowledge and practical skills.
Expert insight, best practices and information on everything related to Observability issues, trends and solutions.
Explore our guides on a broad range of observability related topics.

CI/CD pipelines have become a cornerstone of agile development, streamlining the software development life cycle. They allow for frequent code integration, fast testing and deployment.
Having these processes automated help development teams reduce manual errors, ensure faster time-to-market, and deliver enhancements to end-users. However, they also pose risks that could compromise stability of their development ecosystem.
This article will go over some common CI/CD pipeline security issues and how to effectively overcome them. Plus, learn how to identify vulnerabilities early in development to fully protect your organization’s data health.

There are different threats that could impact your CI/CD pipeline. Such vulnerabilities can be determined and understood based on your pipeline design. Here’s some common CI/CD security risks to watch out for:
Configuring a CI/CD pipeline securely is the first step to reducing risk to your data. While your setup will depend on which tools you use in the pipeline, there are best practices to securing the configuration, such as:
Code vulnerabilities typically stem from using deprecated or insecure libraries. Bad actors can exploit these vulnerabilities to gain unauthorized access to software, inject malicious code, or execute arbitrary commands.
If undetected in the CI/CD pipeline, insecure code leaves your system vulnerable to data breaches, unauthorized access, and ransomware attacks that disrupt your software functionality.
Poisoned pipeline execution is a security risk in CI/CD pipelines where an attacker introduces malicious or compromised code, deploying unauthorized or harmful software components. This can happen at any pipeline stage, including in code repositories, build processes, testing, or deployment environments.
A common attack vector is to modify CI configuration files, adding additional commands to execute code in the CI stage. Once shipped code is executed, attackers can access secrets, ship malicious code, and access private servers or hosts.
CI/CD pipelines can inadvertently expose secrets, such as API keys, database credentials, or encryption keys, leading to severe security breaches if obtained by malicious actors. Secrets can be exposed through:
Test environments sometimes receive a different level of security attention than production environments. They can contain unpatched systems, misconfigured security controls or other vulnerabilities to be exploited.
Breaches in test and development environments can also provide an entry point for bad actors. These external forces could gain unauthorized access and compromise the CI/CD pipeline components.
Implementing pipeline security measures will mitigate CI/CD errors and risks listed above. Having a secure CI/CD pipeline lets you maintain integrity as data moves through your pipeline.
Furthermore, each CI/CD pipeline is unique and should include custom security measures, processes and tools. Here’s how to secure yours:
CI/CD security can be enhanced using a full-stack observability platform to monitor pipeline behavior. Observability platforms can provide out-of-the-box visibility and insights into the security posture of the pipeline, helping DevOps teams understand where vulnerabilities exist.
Observability tools build processes, test environments and deployment stages. Logs containing valuable security information, such as access attempts, system events or errors, are collected and parsed for real-time security analysis.
These tools can then detect and alert DevOps teams of security incidents, anomalies, or unauthorized activities. A comprehensive audit trail can also be established to help organizations meet regulatory requirements and adhere to security policies.
2. Employ tight access control
Use tight access control in CI/CD pipelines so that only authorized individuals and processes can access critical components. Here are some ways to make sure access control is set up securely:
3. Use source composition analysis tools
Source Composition Analysis (SCA) is a security practice that analyzes and evaluates source code composition and dependencies within software applications. SCA identifies and manages the security risks associated with third-party and open-source components used in an application’s codebase.
SCA can identify any known vulnerabilities, licensing issues, or other security concerns that may arise from using third-party code. The tool examines the software’s dependencies, libraries, frameworks, and other external components to assess their security posture. Open-source and proprietary tools are available in CI/CD security implementations.
4. Enforce security policies
Security policies should be clearly defined and enforced for the CI/CD pipeline and software in general. These policies ensure the software is set up and maintained effectively to limit security exposures before they need to be detected in the CI/CD pipeline.
Remember security policies should cover everything from access control and coding best practices to vulnerability and risk management.
Continuous integration (CI) and continuous delivery or deployment (CD) cover the process of automatically merging, building, and testing code changes ready for release, and – in…

The simplest CI/CD observability pipeline consists of three stages: build, test, and deploy. In modern software systems, it is common for several developers to work on…
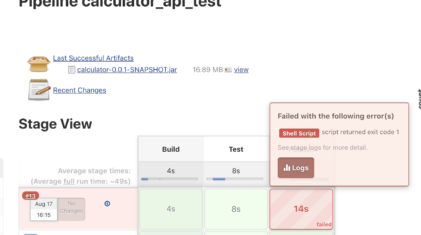
In the previous article, we have created the Continuous Integration (CI) pipeline for a simple Java application. It is now time to start working on the…