5 Cybersecurity Tools to Safeguard Your Business
With the exponential rise in cybercrimes in the last decade, cybersecurity for businesses is no longer an option — it’s a necessity. Fuelled by the forced…
Whether you are just starting your observability journey or already are an expert, our courses will help advance your knowledge and practical skills.
Expert insight, best practices and information on everything related to Observability issues, trends and solutions.
Explore our guides on a broad range of observability related topics.


In late November 2023, a phishing campaign successfully compromised hundreds of user accounts, including those belonging to high-ranking executives, across dozens of Microsoft Azure environments.
Cybercriminals behind such campaigns specifically target executives due to their potential access to sensitive corporate information, the ability to authorize fraudulent financial transactions without raising suspicion, and the potential to gain entry into critical systems that can serve as launchpads for broader attacks within the organization or its partner networks.
This incident is a stark reminder for individuals and organizations to remain vigilant against phishing attempts. Implementing robust security measures like multi-factor authentication and employee awareness training can significantly reduce the risk of falling victim to such scams. Organizations should also consider conducting regular penetration testing to identify and address system vulnerabilities.
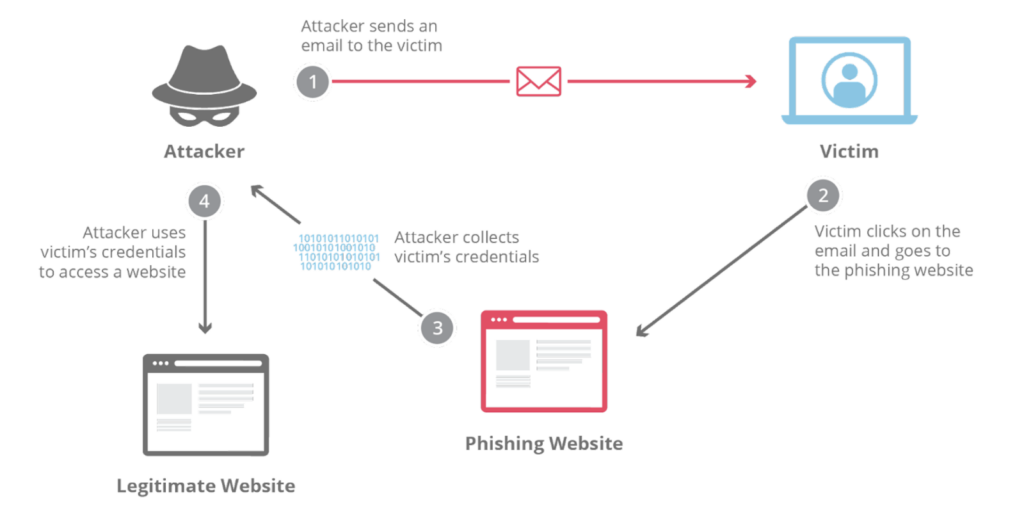
These types of attacks can be quite easy to fall for. The attacker will send an email containing malicious documents or links, including a message of urgency, prompting the receiver to take action. Once the user clicks on the document or link, they will be routed to the phishing pages where the attacker can steal the user’s credentials and information. At this point, the attacker has successfully gained access to privileged accounts and can escalate access to sensitive information and critical systems.
The Breach Attack chain described above was initially detected by security experts at Proofpoint, an email threat management company.
Security analysts uncovered specific Linux user agent strings and domains attackers used to gain unauthorized access to Microsoft 365 applications. These user agents should be a red flag for organizations using Microsoft 365. These IOCs are linked to many post-compromise activities, including bypassing multi-factor authentication (MFA), stealing sensitive data (exfiltration), and launching phishing attacks internally and externally.
Proofpoint identified unauthorized access to critical Microsoft365 components, including:
The malicious phishing campaign targeted a broad spectrum of individuals within numerous organizations utilizing AzureAD.
Not only were senior executives like Vice Presidents, CFOs, and CEOs impacted, but employees across various roles, such as Sales Directors, Account Managers, and Finance Managers, also fell victim.
This widespread attack highlights the need for robust security measures across all levels of an organization, as even seemingly lower-level positions, can grant access to sensitive data and resources if compromised.
The Coralogix security team promptly got into action as soon as this breach was disclosed. They reviewed the Azure environment of our SRC customers for related IoCs and contacted the ones where we witnessed suspicious activity. They also reviewed that all out-of-the-box Azure extension alerts had been appropriately deployed and updated.
For customers using Azure, it’s best to monitor logs for the specific user-agent string shared above and suspicious source domains. It’s best to immediately reset passwords for compromised accounts and change all user passwords periodically.
Use security monitoring tools to detect and identify account takeover attempts. Implement industry-standard protections against phishing, brute-forcing, and password-spraying attacks. Lastly, implement automated threat response policies for faster reaction and damage control.
You can learn more about what you can gain from the Coralogix security offering here.

With the exponential rise in cybercrimes in the last decade, cybersecurity for businesses is no longer an option — it’s a necessity. Fuelled by the forced…
AWS VPC Flow Logs monitor and record details about the traffic passing through your application, including requests that were allowed or denied according to your ACL…
The wide-spread adoption of cloud infrastructure has proven to be highly beneficial, but has also introduced new challenges and added costs – especially when it comes…